Example use-case
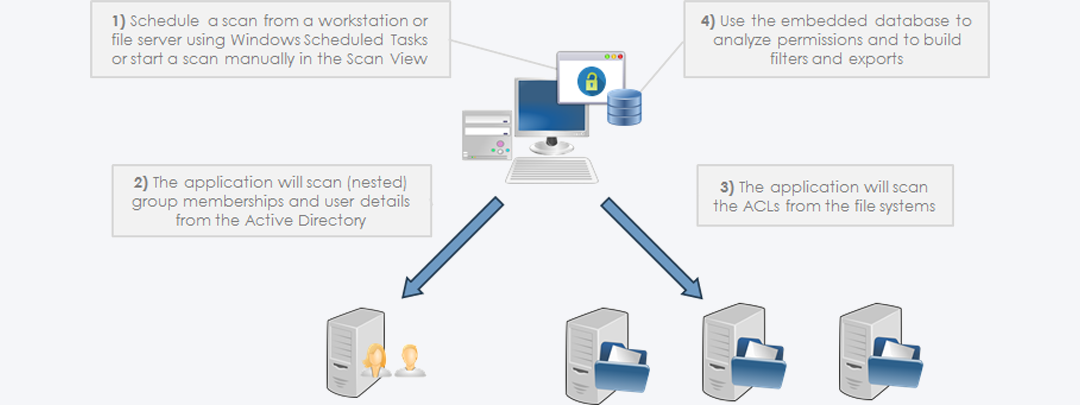
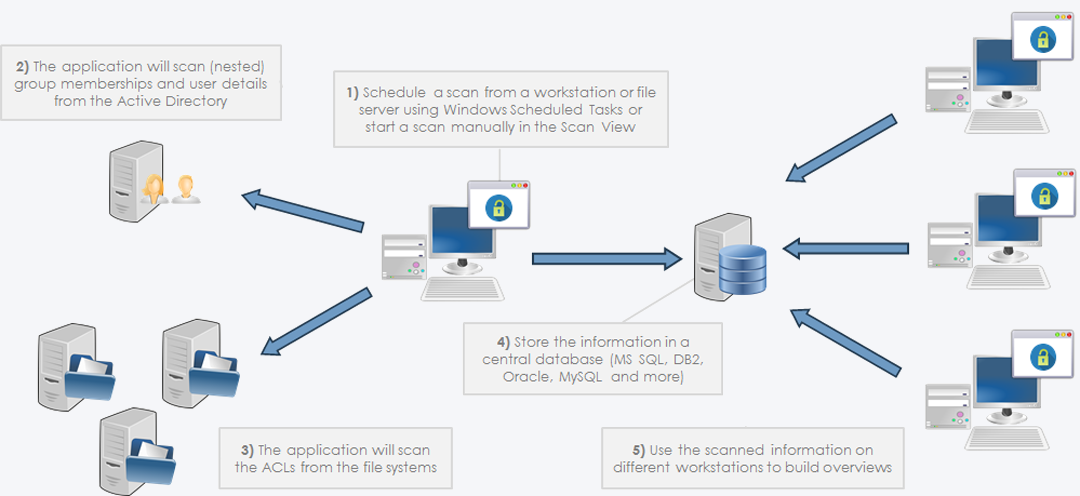
More than ten years ago, Permission Analyzer started as an application to reveal the NTFS rights per user or group. Now, the application has been completely rebuilt to version 2, in order to better fulfill information requirements. Permission Analyzer was rebuilt with the focus on performance and large amounts of data. The directory information and user information is therefore not all loaded into memory and it does not scan the network for every search, but it uses a database to gather all the information together and to apply filters. It’s standard to use an embedded database (H2), but out-of-box the application also supports MSSQL Server, Oracle, MySQL, DB2, PostgreSQL and Derby.
Scanning the network
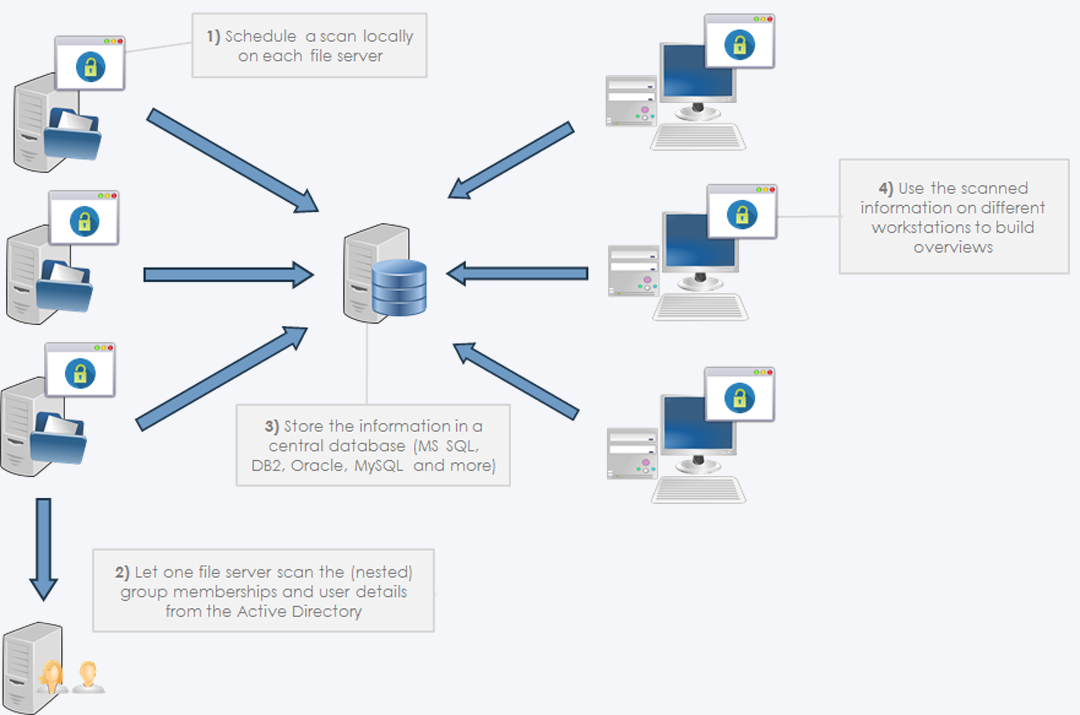
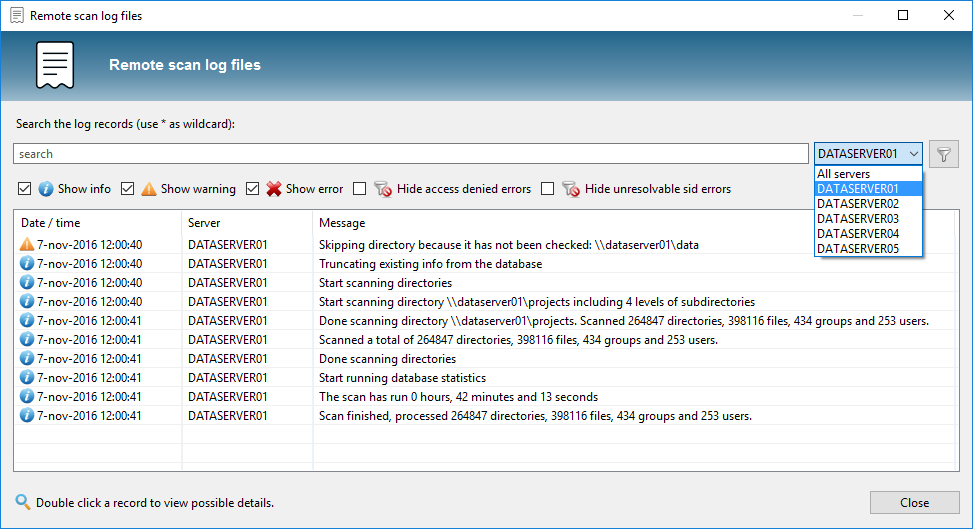
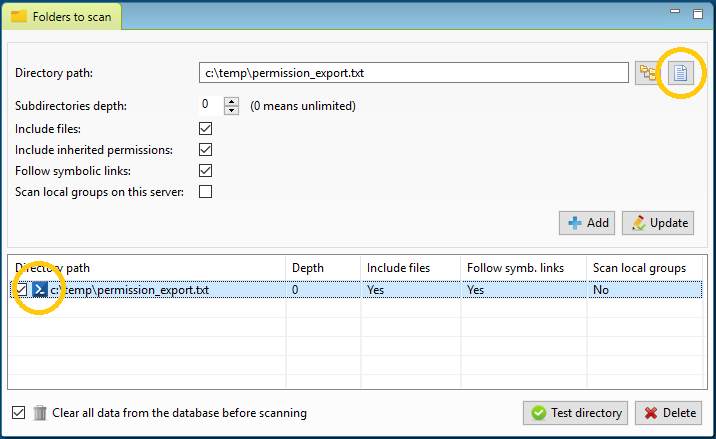
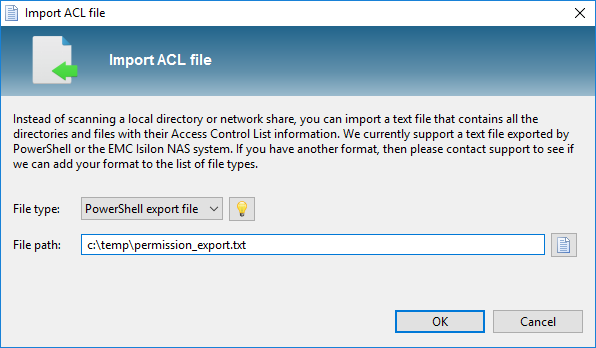
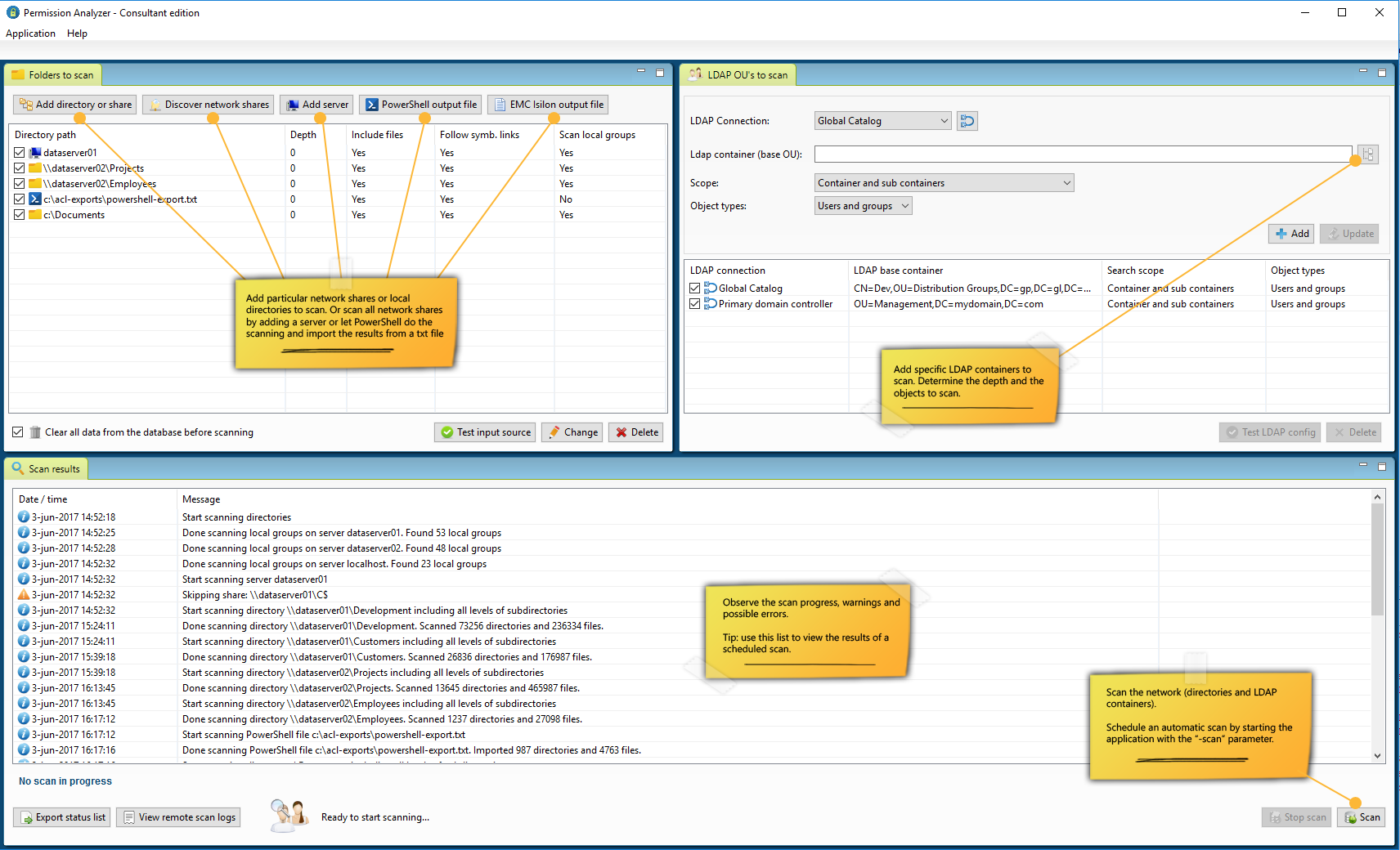
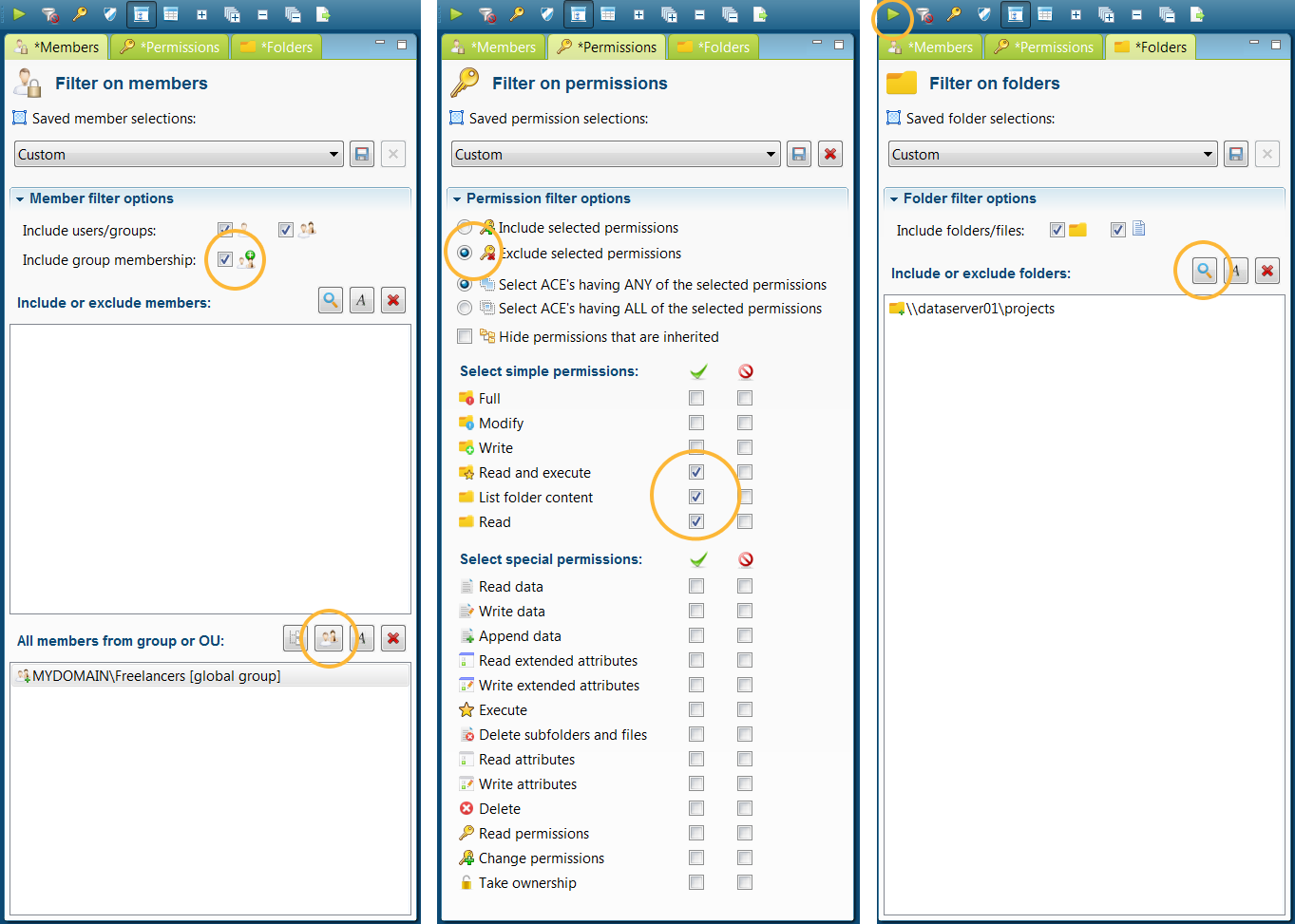
The application provides two ‘views’ from the menu, the Scan View and the Report View. In the Scan View the scan is configured by selecting the desired directories and OU’s from the Active Directory. The directories can be added as network share, local directory, simply a server name (a search for network shares will automatically happen), or a text/zip file generated by a Powershell script included or EMC Isilon export from a NetApp filer. Incidentally, a Scan Agents can also be used that run locally on a file server and store the scan results in a central database. The Active Directory OU’s are used to scan for group memberships. A scan can also be started automatically with various command-line parameters, which periodically refreshes the data.
Creating reports
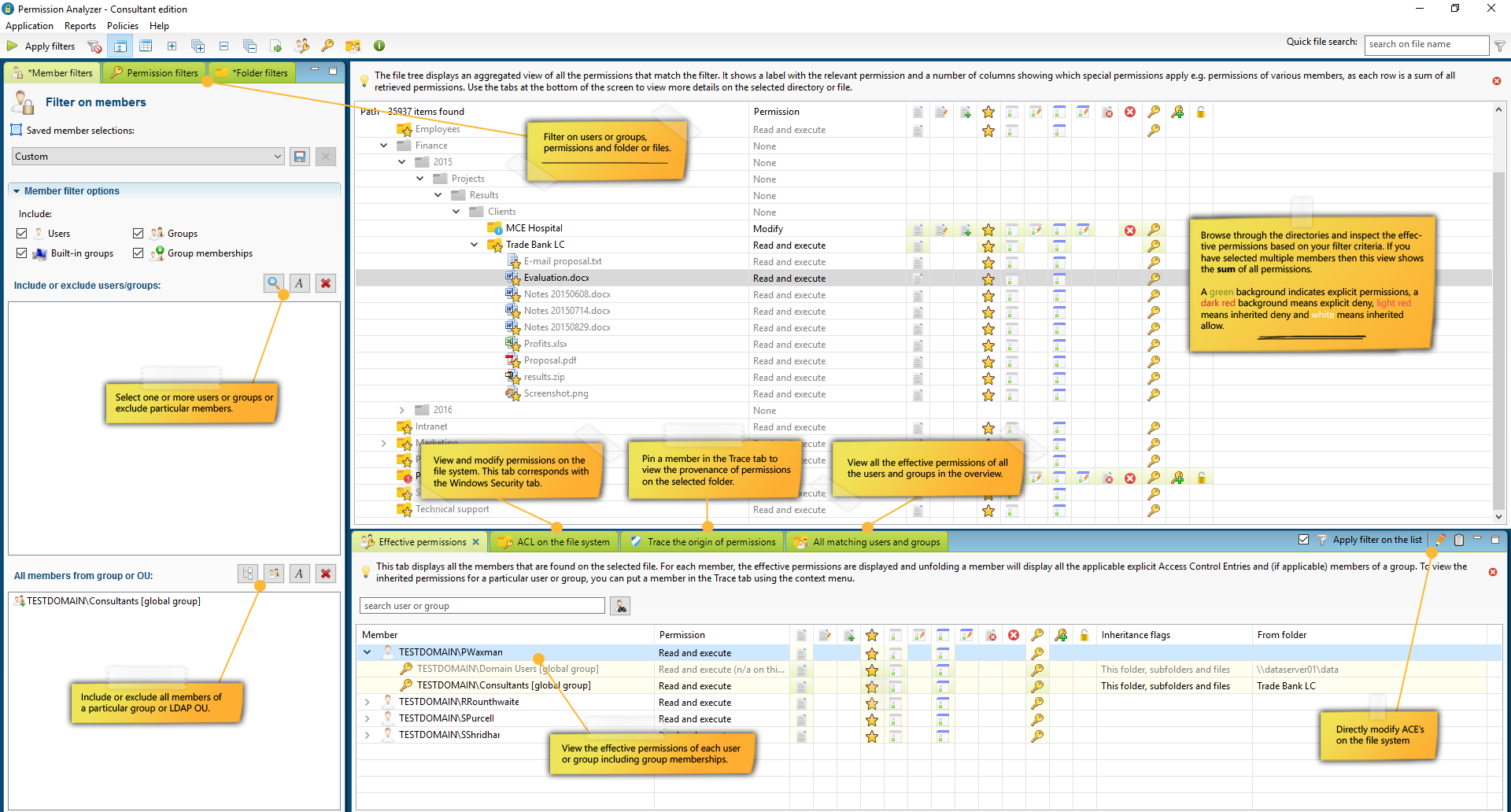
After the scan is complete the database can be used to make overviews. The Report View of the application displays the initial folder tree containing a summation of the rights found per directory or file. The folder icon indicates what rights are found and the columns next to a directory show the special rights. Without applying filters, the permission will mainly be set to “Full Control” with all the special rights, but after applying filters on a user or group, the unwanted rights can be viewed at a glance. In order to not clutter the folder tree the users are not instantly displayed in the folder tree, but rather across in four tabs under the folder tree:
- Effective permissions: displays the effective rights of all users and groups in the selected folder that match the filter criteria. Each user or group can be folded out to see where the rights originate from.
- ACL on the file system: shows the rights (Access Control Entries) as they appear on the file system. This corresponds with the Security tab in Windows Explorer and includes the possibility to adjust rights from within the application.
- Trace the origin of permissions: provides the ability to create a user or group to pin down through which group memberships and parent folders the rights have been obtained.
- All matching users and groups: the previous tabs display information for the selected directory. This tab displays all unique users and groups that are found in the overview. Each user or group can be folded out to see where the rights are found and through which group.
Through these four angles we can easily get answers to different information requirements. We can instantly view effective rights on all directories, we see per directory and user where the rights come from and we can filter out all the users of a particular group without losing the relationship between the rights and users. The latter helps us with the information requirement (“What are the right for all users of a specific group and where are the exceptions?“). Finally, we want to know which users or groups are involved in the unwanted rights within the search results. By including multiple users/groups as a filter, or a filter of the “All members from group” type, in one bulk check an overview is created for a large group of users including nested group memberships. With the "Effective Permissions" and "All matching users and groups" tabs, we can subsequently zoom in on individual users.
The last information requirements is to run checks to keep the access rights consistent. Instead of notifying system administrators for each change, Permission Analyzer offers another solution. A set of filters can be stored as Policy in order to periodically check for unwanted rights. If search results are found on a Policy, the system administrator can be notified by email, with an HTML report of the rights found as an attachment. Also, the list of Policies with their status is available within the application. Loading of a Policy gives the possibility to zoom in on the results and thus solve the cause.
Example of an audit policy
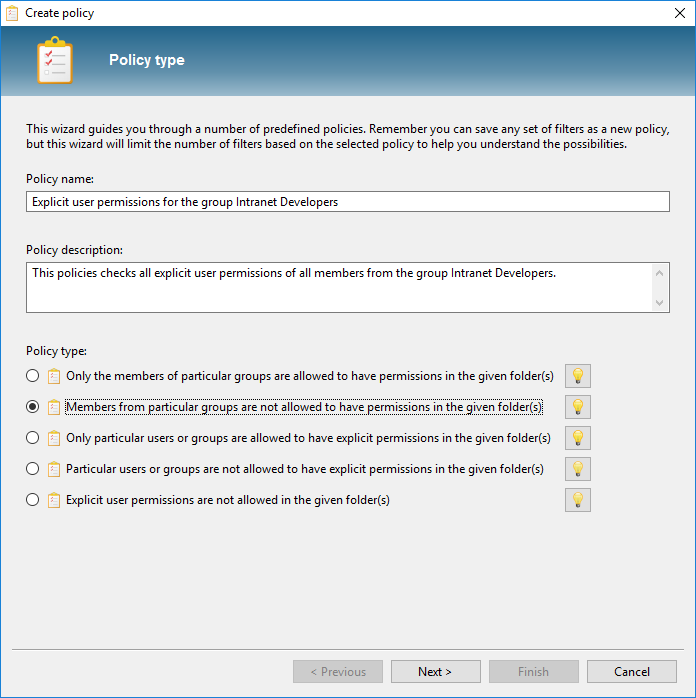
We make a policy in which it is stated: “Nobody from the group Freelancers can edit project data”
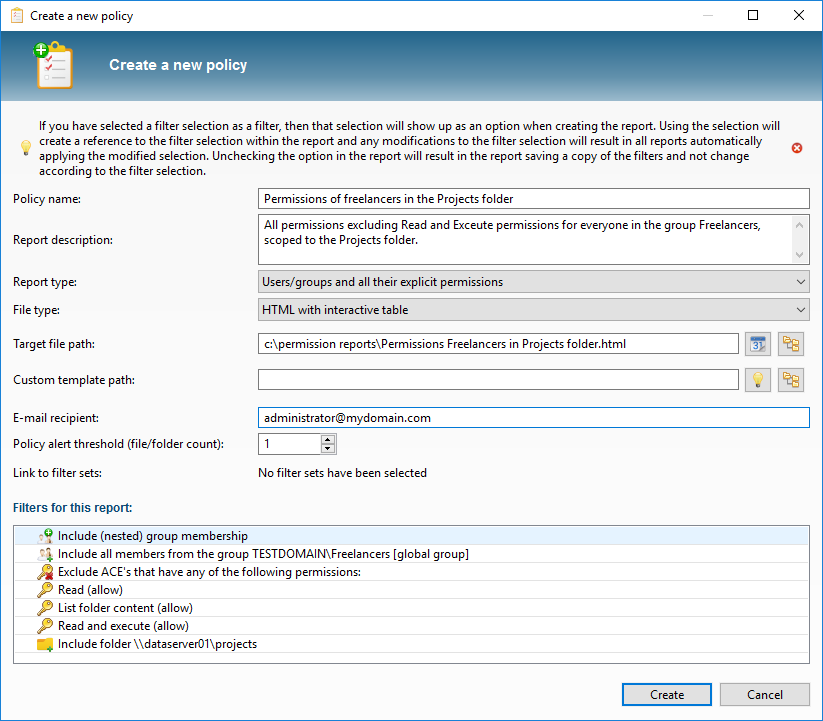
We want to create a report in which we get to see the unwanted rights so that we can save the filters as Policy. We add a member filter of the type “All members from group” and we select the group Freelancers. Then we add additional filters to the rights (we want to allow read access), and we report on the scopes folder \\dataserver01\projects:
Tip: Use the Policy Wizard to get acquainted with the various filter options:
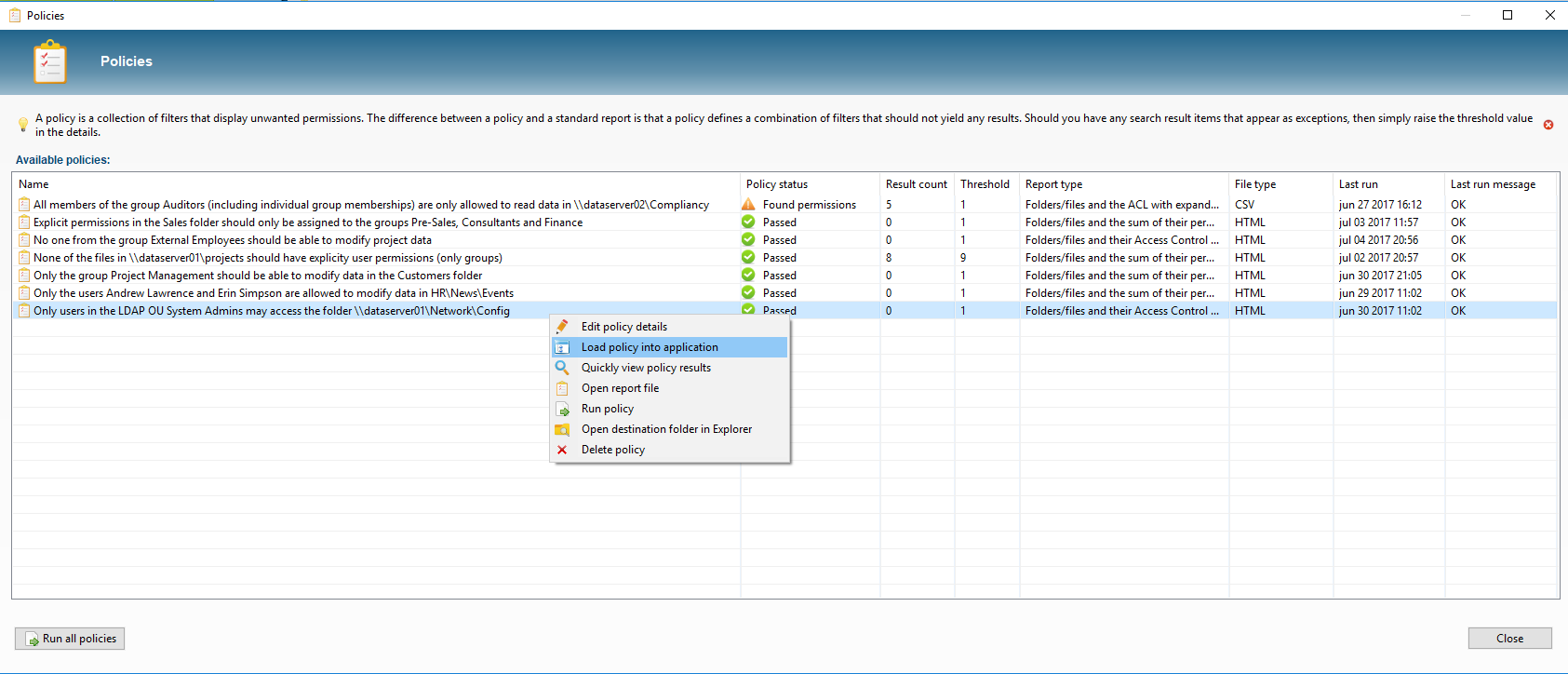
The listing now shouldn’t display any search results, which means that no unwanted rights have been found. We now store the filters as Policy:
By regularly running the policies via the parameters -scan and -allPolicies, we can periodically check the rights for consistency, without having to check each change in the folder structure manually. In the overview of Policies we can see the status of our rules at a glance and we can zoom in on the unwanted rights by loading a policy in the application:
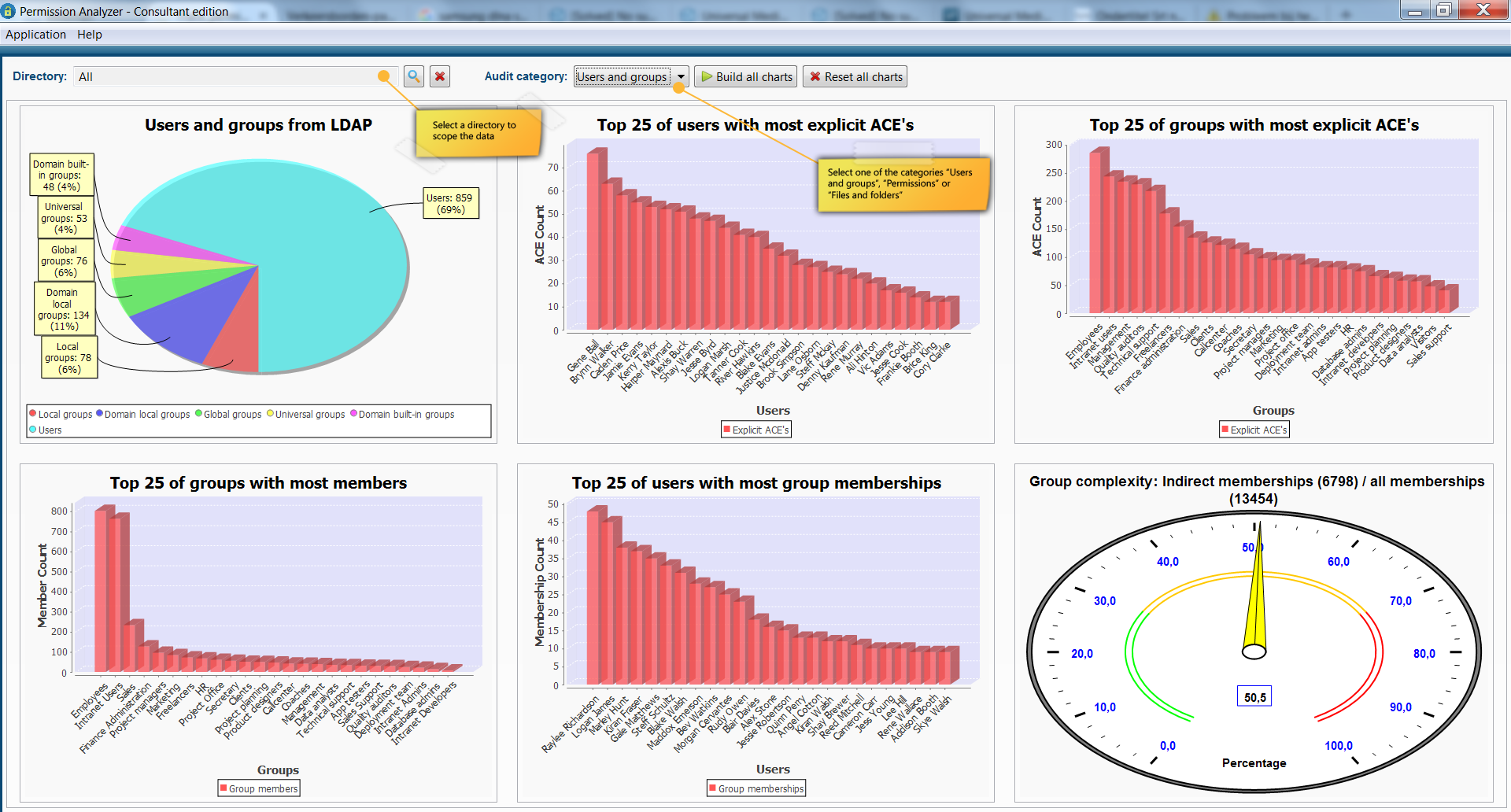
In addition to regularly running policies we can immediately discover a number of improvements for the Data Access Governance via the Audit Permission Analyzer’s dashboard. This dashboard shows 18 different charts including a top 25 of users who have the most explicit rights (rights that may have to be regulated through a group membership), a top 25 of users with the most group memberships, the ratio between direct and indirect group membership, directories with the most explicit rights and much more. Many of these statistics instantly detect where the possible risks are if someone manages to get unauthorized access to the system.